1. Preparation time
- Once you get your additional ISP line, plug a laptop to the router/modem and find out what local IP address and gateway address you will get. In our case, the local IP give to my laptop was 192.168.70.2 (255.255.255.0 = /24) and the gateway is 192.168.70.1/24. This means that the IPv4/CIDR block is 192.168.70.0/24.
- Plug in a cable to your Proxmox router box and remember which port number that is. In my example, I use Qotom and plugged it into port 2, which translates as ‘enp2s0’.
2. Add another virtual bridge in Proxmox
- In Proxmox, go to your node -> System -> Network, find your primary LAN interface (e.g. vmbr0) and remove the port that will now be used for WAN 2 connection.
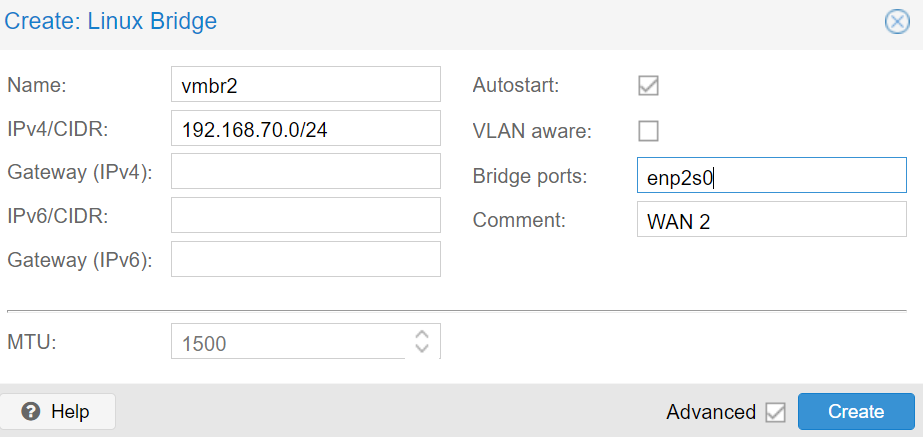
- Then add a new bridge (since ‘vmbr1’ is likely already used for WAN1, it would likely be ‘vmbr2’). Add the IP range that the WAN 2 router gave you (CIDR is the whole block range with the network mask) and gave it a name such as WAN 2.
- Add the network bridge to the OPNSense VM. Edit the VM and under ‘Hardware’, add a new Network device. Choose the correct interface (e.g. vmbr2). Choose model as VirtIO (paravirtualized) and untick the Firewall field.
- Restart your Proxmox node. It is recommended to manually shutdown VMs that run database services to ensure that there is no data loss (esp. if you do not have a QEMU agent installed on each VM).
3. New interface set up in OPNSense
- After the Promox restart, log into the OPNSense and go to ‘Interfaces’ -> ‘Assignments’. Notice the new interface – give it a name and enable it.
- Then go to the WAN2 interface and enable it. Tick the boxes for ‘Block private networks’ and ‘Block bogon networks’. Unless you have a static assignment, select DHCP to be used on that port (your ISP router/modem will provide the IP).
- Check that the new WAN interface is active. In OPNSense, go to ‘System’ -> ‘Gateways’ -> ‘Single’ and check that WAN 2 appears there as active and that you have received an IP address. Note that depending on the configuration of the ISP router, this would be either an external or internal IP address. If you get an internal IP address, there is a possibility that in case you want to host any websites on it, you will need to ask your ISP to assign you a static IPv4 address, which typically costs a few dollars a month.
- While in ‘System’ -> ‘Gateways’ -> ‘Single’, find your WAN 1 interface and edit it by clicking on the pencil sign. Under ‘Monitor IPs’, add 8.8.8.8 . Uncheck the ‘Disable Gateway Monitoring’ option. Save and apply the changes.
- Do the same for WAN2 with the exception of setting the monitor IP as 8.8.4.4 (the secondary Google DNS server). Of course, you can use something else such as 1.1.1.1 .
4. Gateway grouping & policy-based routing for multi-WAN set up
- In OPNSense, go to ‘System’ -> Gateways -> Group and add click on the ‘+ Add’ button.
- Choose Tier 1 for your main WAN and Tier 2 for your backup WAN. Ignore the others. Trigger level should be packet loss. Then click on the ‘Save’ button and t hen on ‘Apply changes’.