Create promote to admin and demote to standard user scripts
- First of all, in JamF Pro, go to the Management Settings -> Scripts -> click on the + sign to add a new script.
- As a Display Name, call it something like ‘Promote current user with admin rights’.
- In the script section, add the following simple script where we identify the username and promote that user to be an admin.
#!/bin/sh
U=`who |grep console| awk '{print $1}'`
# give current logged user admin rights
/usr/sbin/dseditgroup -o edit -a $U -t user admin
/usr/local/bin/jamf displayMessage -message "Your account has been granted Superuser rights for 48 hours. Please remember - With great power comes great responsibility."
- Then create another script and call it something like ‘Demote current user to a standard account’.
- The script checks if the user is already an admin and if yes, it will change the account type to ‘Standard’ and display a message to the user. See below. We are yet to create a policy to define when it will be launched.
#!/bin/sh
currentUser=$(ls -l /dev/console | awk '{ print $3 }')
if [ $currentUser != "sifi" ]; then
IsUserAdmin=$(id -G $currentUser| grep 80)
if [ -n "$IsUserAdmin" ]; then
/usr/sbin/dseditgroup -o edit -n /Local/Default -d $currentUser -t "user" "admin"
/usr/local/bin/jamf displayMessage -message "Time is up, super-user rights were revoked"
exit 0
else
echo "$currentuser is not a local admin"
fi
fi
Create credentials for API access in JamF Pro
In order to be able to talk to our JamF Pro instance, the first thing we will need is to clarify what is our instance’s URL and what username and password can be used for API access.
- Create a username and password for API access in JamF Pro:
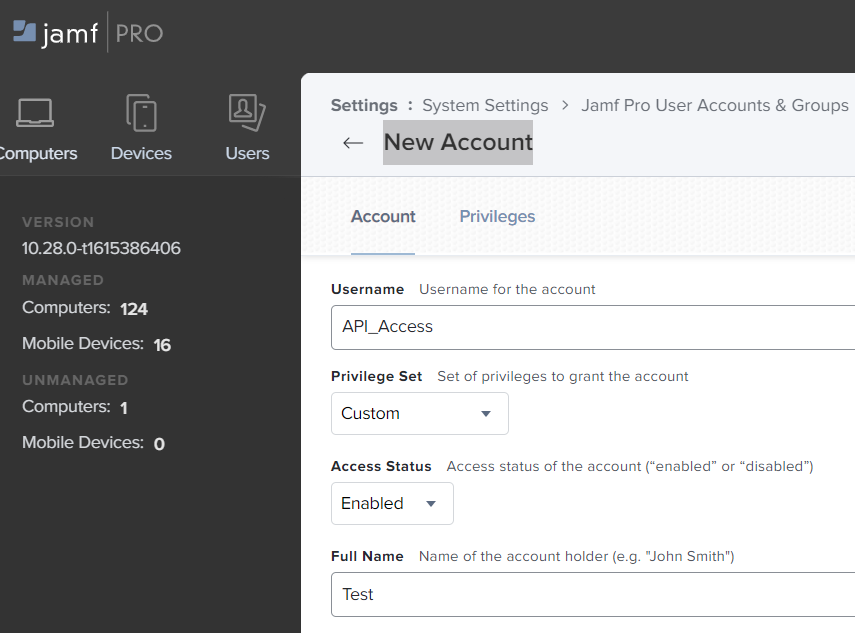
- Log into your JamF Pro instance and go to ‘Management Settings’ -> ‘System Settings’ -> ‘Jamf Pro User Accounts & Groups’.
- Create a new Standard Account such as ‘API_Access’ and set privileges to ‘Custom’.
- Leave ‘Access Status’ as enabled.
- Fill in the other fields such as name and password.
- Confirm by clicking on the ‘Save’ button.
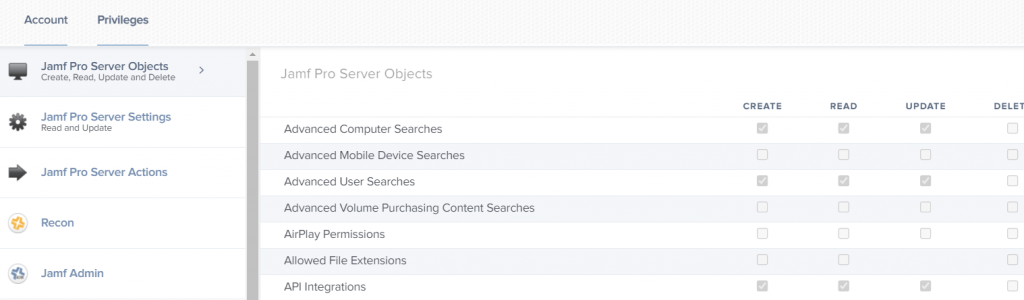
- Assign the new credentials API-related privileges:
- Assign access to this account based on what actions you will need to perform with it. For example, if you want it to perform advanced computer searches , then find the item with the same name and tick the box in the second column for read-only permissions.
- Generally, it is recommended to grant read-only permissions for ‘Users’ (to be able to look up user IDs), read-only+update permission for ‘Computers’, grant read+update Static User Groups and have read-only access to ‘Policies’ – but all of this very much depends on the tasks you are looking to perform.
Create an initial workflow in Integromat
- Note the following potential responses to an API call:
- 200 – OK, the call was successful with some returned value
- 201-202 – Created / Accepted
- 400 – Bad Request – something is wrong with how you defined the request
- 401 – Not Authorized – the credentials you supllied do not have the required rights
- 403 – Forbidden – invalid credentials supplied
- 404 – Not found – what you asked for cannot be found
- 500 – Internal server error
- 502 – Bad Gateway – the API server is not reachable or does not provide the required functionality. Check what hostname you are using
- 503 – Service Unavailable – service is not available to you. Potentially, you got error 401/403 too many times and got temporarily banned
Now since we were able to send the request from Postman, let’s now try to do the same and more from Integromat!
Sources
- JamF Pro’s official API guide
- TalkingMoose’s script for setting computer pre-stage scope
- GeekyGordo’s (Steve’s) article on Using Postman for JamPro API Testing
- MyIntervals’ API error codes