- Just to repeat from earlier, with HAProxy in place to decrypt incoming SSL communication, in order to access RoundCube on what seems from the mail server’s point of view as HTTP, you need to disable the force_https directive in the Roundcube config file:
sudo nano /opt/www/roundcubemail/config/config.inc.php # Find this part under //SYSTEM $config['force_https'] = false;
- Access the web interface on https://mail.your-domain.tld/mail/
- Try logging in with the details you created earlier in the iRedAdmin interface.
- You can observe your login (or a failure to login) by looking at the end of this file:
sudo tail -n 3 /var/log/mail.log
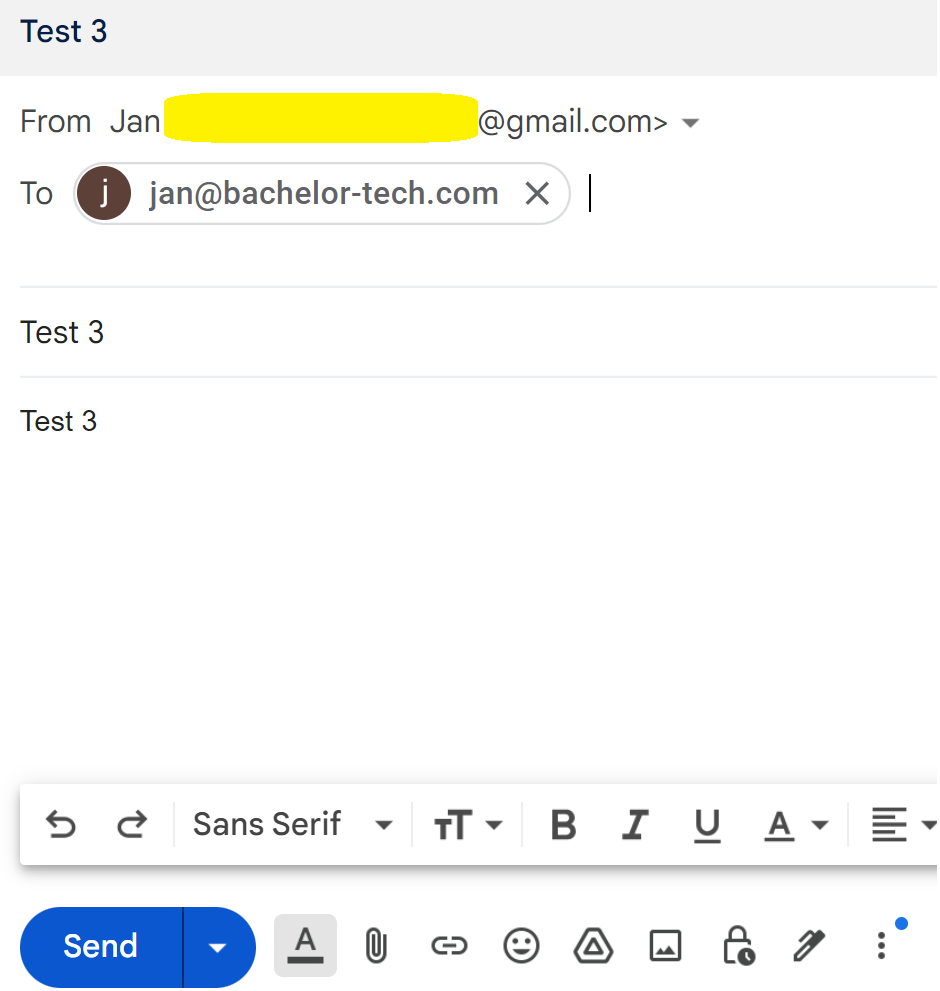
- At this point, you can try sending an email to your new mailbox from outside – providing that port 25 on your firewall is unblocked and points to the IP address of your mail server on the LAN.
- If the email is not arriving into your mailbox and there is nothing in the
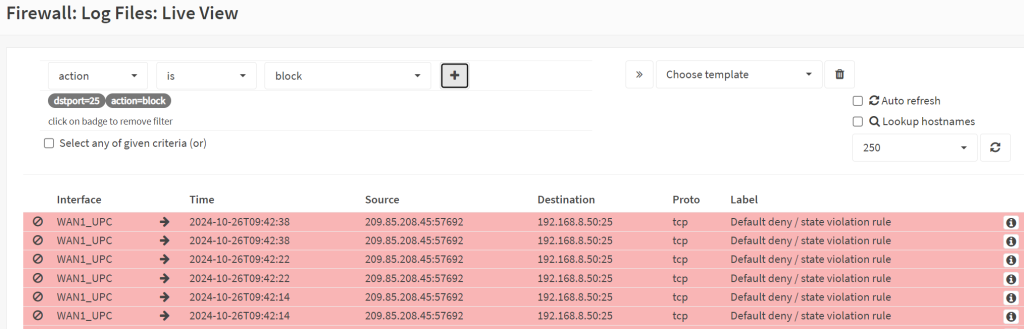
/var/log/mail.logfile, it is likely being blocked by your firewall.- If you use OPNSense, you can check it in the section called Firewall → Log files → Live view.
- Expand the view to at least a 100 items and watch it as you send an email to your mailbox.
- Add two filters – one that is ‘Action – is – block’ (click on the + sign) and then one that says dst_port (destination port) – is – 25 (again click on the + sign).
- If you see repeated attempts to reach port 25 then you know that your firewall rule is not set up correctly.
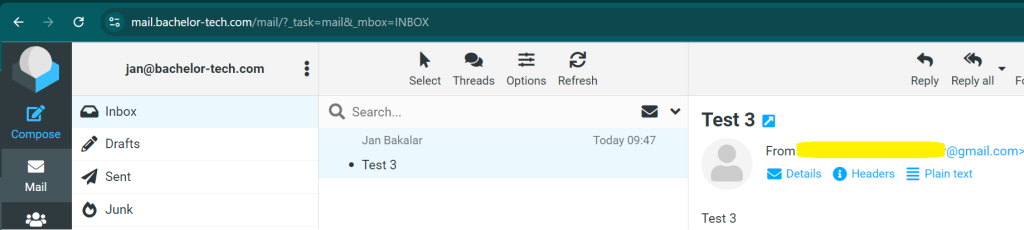
- If the email arrives correctly, you will be able to access it in RoundCube:
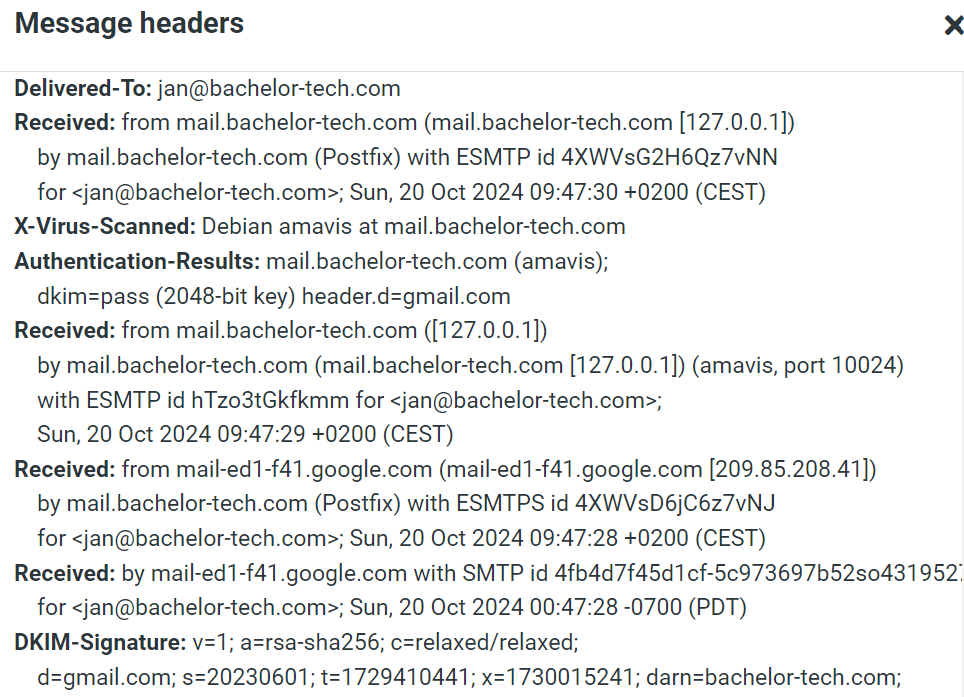
- You can review the test mail’s header to confirm that amavis service on our mail server provided virus scanning (together with SpamAssassin):
This does not yet mean that you can send emails out, as your mail server and domain does not have its own DKIM, SPF and DMARC DNS records set up, nor have we have set up an SMTP relay yet. So let’s start working on SSL for non web services, (although we might as well apply the certs for Nginx as well).